Identity Detection and Response (IDR)
Prevent compromised identities so data and systems stay secure.

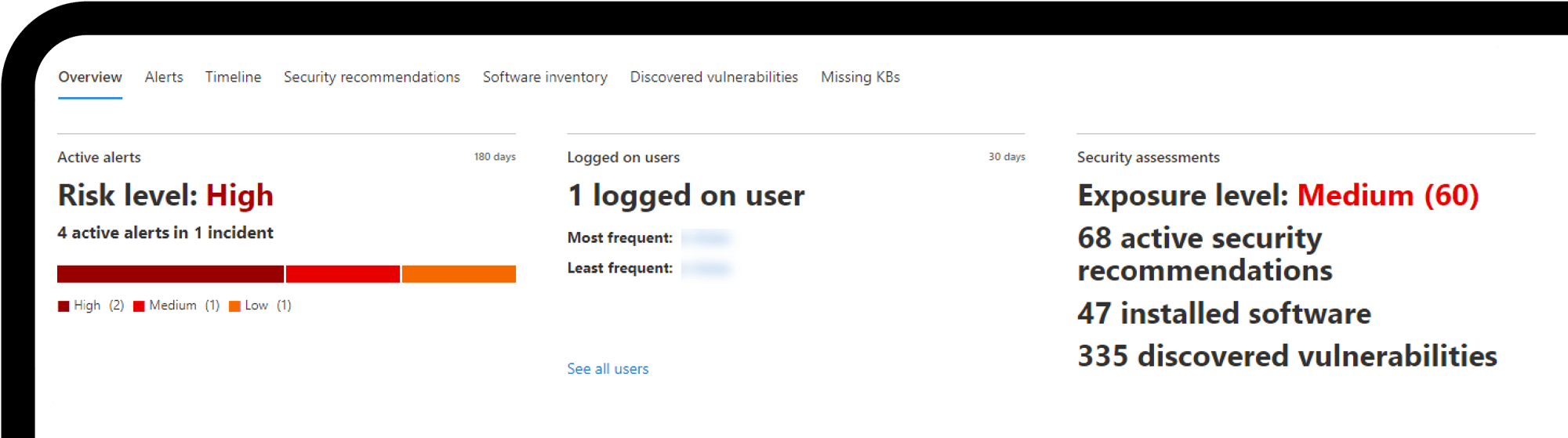
Total Identity Threat Visibility & Response
ProArch's Security Operations Center (SOC) keeps watch 24/7/365 to stop account compromises and credential-based threats.
We not only enable your organization to protect against identity threats in real-time but also to proactively stay ahead of them with a stronger and more resilient security posture.

.png?width=80&height=80&name=Untitled%20design%20(8).png)
ProArch's Identity Threat Detection and Response

What's Covered

What's Included


Is IDR right for you?
If you answer 'yes' to these questions, we should talk.
Users regularly work in different locations and countries?
Has a compromised identity resulted in data loss?
Did privilege escalation lead to a ransomware attack?
Lacking threat investigation and response skills?
Identity and access management (IAM) needs to be enhanced?
Identity security access controls, SSO and MFA, not in place?
Seeking strategic guidance for long-term risk reduction?
Required to adhere to regulatory compliance requirements?

Access Permission Approvals
Time-based and approval-based role activation alerts are enabled to mitigate the risks of excessive, unnecessary, or misused access permissions on critical resources.

Block Risky Log-in Attempts
We implement access control policies to mitigate risky log-in attempts by blocking or requiring multi-factor authentication challenges.
“For us, it came down to, ‘Who do we think the best long-term security partner is going to be?’ The answer to that question is ProArch.”
-CIO, Healthcare


