Data Security Reinvented: The Role of Microsoft Purview
In today’s modern workplace, data security risk is dynamic. The type of content changes, just as the people who interact with that data shifts. What people do with data changes too. That means data security is even more complicated to manage.
Broad, static policies no longer work; at one extreme, they run the risk of not doing anything and on the other, they can overprotect data to the point that people can’t get anything done at all. Far too often, admins scramble to manually adjust policy scope and triage alerts to identify critical risks.
The key to data security is securing data anywhere it happens to go. That’s where Microsoft Purview can help. Keep reading to see how Microsoft 365 Purview helps secure data wherever it lives, prevents data loss with the right policies, and manages insider risk.
How secure is your data?
Do you know what kinds of sensitive data you have and where it lives? How are you currently securing sensitive data across all your environments and preventing its loss? And how do you manage insider risks? These are all questions today’s businesses need to be asking.
The fact is, data security is hard. You need to secure emails, messages, shared storage, and cloud apps—not to mention all the devices that data is accessed on. Plus, the average company’s data footprint keeps growing exponentially.
It’s a conundrum, and today’s organizations are struggling with a fragmented solution landscape. More than 80% of decision makers purchased multiple products to meet compliance and data security needs. However, this approach can be costly, hard to manage—and still leave gaps.
Where do data security incidents come from?
Data security incidents can happen anytime anywhere. There are three primary scenarios for data security incidents: 1) If your organization doesn't have visibility into it's data – the data is at risk of misuse (exfiltration, exposure, etc.). 2) If a user has malicious intent and is trying to exfiltrate the data and 3) If a user inadvertently takes a sensitive document and makes it visible.
But regardless of when and how that data was exposed the larger issue is that most organizations have no visibility into how their data is being used and accessed. And without visibility, you just don’t know what your risk is.
Elements of a Data Security Strategy

As organizations think about protecting their most important asset, their data, they ultimately need to create a defense in depth approach around it. There are three components to a data security strategy, and they should be tailored to your own organization’s unique needs.
- Let’s start with protecting sensitive data. It is important to understand and discover sensitive data within your organization so protection policies can be put in place to keep that data safe. You need visibility into your entire data estate, whether on-prem, hybrid, or multi-cloud.
- Data doesn’t move itself; people move data. With all data in organizations, you need to understand the user context and intent around the data to effectively protect it with the right policy. This next layer of defense takes into account user context to identify potential data risks and/or risky activities that may lead to data security incidents, enabling security teams to quickly take mitigating action. Since data loss is usually caused by internal actors, organizations need to take a holistic approach to managing insider risk, which brings together the right people, processes, training and tools.
- The last layer of defense is to prevent data loss or unauthorized use of data. Organizations need a way to balance protection and productivity, without compromising either. It’s critical to ensure the proper access controls are in place and policies are set to prevent actions like improperly saving, storing, or printing sensitive data.
What is Microsoft Purview?
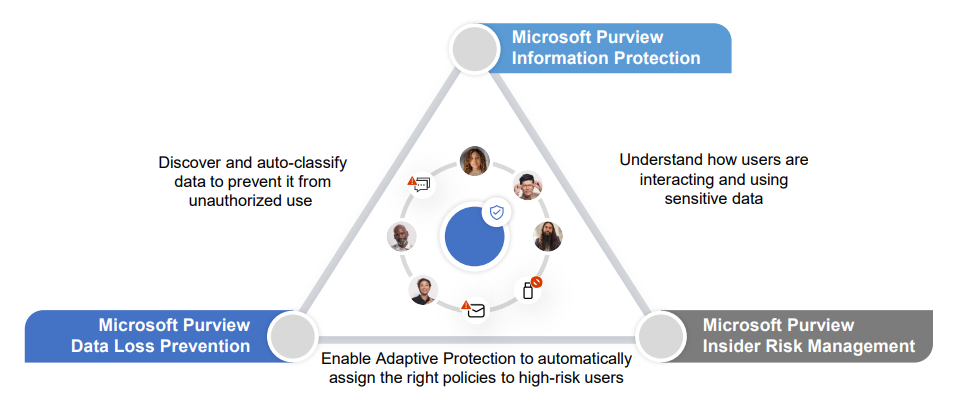
Microsoft Purview strengthens data security by bringing together information protection, insider risk management and data loss prevention (DLP) into a single platform. Microsoft Purview is made up of three different layers of protection that don’t just help to secure data from potential data security incidents, they also work together to strengthen data security and reduce the security team’s workload.
- Protect sensitive data with Microsoft Purview Information Protection. Information Protection offers visibility into where your data lives, classifies sensitive information through comprehensive labeling, and applies built-in encryption to protect your data.
- Prevent data loss with Microsoft Purview Data Loss Prevention (DLP). DLP provides controls to prevent data loss or unauthorized use of that data, such as improperly saving, storage, or printing.
- Manage insider risk with Microsoft Purview Insider Risk Management. Insider Risk Management provides user context around data and applies built-in, ready-to-use machine learning models to detect and mitigate the most critical data security risks around that data.
Think of it this way. If you use Information Protection and Data Loss Prevention (DLP) together, you can discover and auto-classify data to prevent unauthorized use. Similarly, using Information Protection and Insider Risk Management together helps you understand the user intent around sensitive data to identify the most critical data risks in your organization.
If you use Insider Risk Management and DLP, you can enable what is known as “Adaptive Protection,” which assigns appropriate DLP policies based on user’s risk levels. With Adaptive Protection, you can understand the context in which users are accessing information and how they’re interacting with it. Then you can calculate and assign appropriate risk levels, and automatically tailor the appropriate DLP controls based on a user’s risk levels. And when you put them all together, you have stronger data security.
Microsoft Purview also integrates with the most commonly-used Microsoft 365 productivity tools, such as Teams, Exchange, SharePoint, and OneDrive, so users get appropriate nudges as needed and can take actions to help protect data responsibly.
Isn’t it time to secure your data?
In today’s world, there are no geographical limits to sensitive data; it travels across people, places, and devices around the world. The key to data security is securing that data anywhere it happens to go.
As a top Microsoft Partner, ProArch’s uses Microsoft Purview to build holistic data security strategies for today’s global, regulatory, and modern business landscape. Contact us for more details.

Director of Marketing Rebecca leads ProArch's marketing efforts, seamlessly blending technology and storytelling to assist clients in their buying journey. She is dedicated to presenting technological solutions in a compelling manner that drives significant growth for the company. Collaborating closely with sales, engineering, leadership, and HR teams, Rebecca sets the strategic vision for ProArch and ensures alignment across the organization. Her strategic, visionary, and detail-oriented approach shapes ProArch’s brand to be synonymous with reimagining technology to achieve business objectives.

