Managed Detection & Response (MDR) Services
24/7 Managed Detection, Investigation, and Response for all size business
View MDR Plans View MDR Comparison GuideManaged Detection and Response (MDR) Services
ProArch’s 24/7 Managed Detection and Response Services is a turnkey solution for threat detection, investigation, containment, and response.
Whether you have 50 or 5,000 users, you gain industry leading solutions and highly skilled professionals that are on your side every day in the fight against security threats.
Endpoint Detection and Response (EDR)
Keep threats off devices that are a clear path to corporate resources.
- 24x7 response to endpoint threat activity
- Endpoint monitoring and detection
- Coverage for workstations, servers, and mobile devices (Windows, Linux, MacOS, iOS, Android)
- Seamless escalation to Incident Response
Identity Detection and Response (IDR)
Prevent corporate account compromises that lead to data breaches.
- 24x7 response to suspicious account activities
- Identity monitoring and detection
- Coverage for on-premises and cloud-native corporate accounts (Active Directory)
- Seamless escalation to Incident Response
Extended Detection and Response (XDR)
End-to-end attack prevention across networks, endpoints, and identities.
- 24x7 response to threat activity across on-premises and cloud networks, endpoints, and identities
- Endpoint, identity, and network monitoring and detection
- Coverage for Azure, Google, AWS
- Seamless escalation to Incident Response
*Extended Detection and Response (XDR) must include Endpoint Detection and Response (EDR).
What is MDR?
Managed Detection and Response (MDR) is a 24/7 outsourced cybersecurity service that provides continuous threat monitoring, investigation, containment and rapid incident response.
ProArch delivers Managed Detection and Response (MDR) services for all size businesses that require continuous threat detection, investigation, and rapid response without the cost and complexity of building an in-house SOC.
Our 24/7 Security Operations Center (SOC) analysts operate as an extension of your security team, identifying and containing threats before they impact business operations, data integrity, or brand trust.
99%
Alert Noise Decrease
Real-time
Critical Vulnerability Notifications
5 Minutes
Average Time to Respond
Is MDR right for you?
Cybercriminals Strike Strategically & Fast
The window of time to detect threats is getting shorter before damage spreads.
Missed Threat Signals & Too Many Alerts
Siloed or misconfigured tools adds to the confusion of where to focus and when.
24/7 Monitoring & Response is Not Optional
The decision lies between building the program internally or outsourcing it.
Actionable threat insights from ProArch’s SOC team
How Digital Currency Mining is a Growing Silent Threat in 2026
Read MoreMDR Service Plans for Security Needs
Choose the MDR plan that fits your risk profile, compliance requirements, and security maturity.
MDR Core
Essential coverage and response capabilities
- Endpoints
- Cloud Identity (Human, non-Human)
- Email & Collaboration
- Cloud Application (SaaS, GenAI)
- Extended Detection & Response
- Monthly Reporting
MDR Premier
Comprehensive security coverage and strategic guidance
MDR Core
- On-Prem Identity
- Managed SIEM
- Cloud & AI Workloads
- Operation Technology
- Quarterly Reporting
- Threat Hunting
- Dedicated Security Advisor
- Executive Business Reviews
MDR Premier
Complete security program in a box
MDR Core
MDR Premier
- Security Awareness Training
- Phishing Campaigns
- Vulnerability Scanning, Reporting
- Annual Penetration Testing
What Managed Detection and Response Services Cover
ProArch MDR provides continuous monitoring and response across endpoints, identity, cloud, and AI workloads using Microsoft Security tools.
Endpoint
- Servers
- Workstations
- Mobile Devices
Tools:
Microsoft Defender for Endpoint
Microsoft Defender for Servers
CrowdStrike Falcon EDR
Identity
- On-premises
- Active Directory
- Azure
- Entra ID
Tools:
Microsoft Defender for Identity
Microsoft Entra ID
CrowdStrike Falcon Identity
Collaboration
- Exchange Online
- Teams
- SharePoint
- OneDrive
Tools:
Microsoft Defender for Office
Cloud
- Azure
- Amazon Web Services
- Google Cloud Platform
- AI & Data Workloads
Tools:
Microsoft Defender for Cloud
Cloud Apps
- Microsoft 365 Apps
- Third-party Cloud Apps
Tools:
Microsoft Defender for Cloud Apps
SIEM
- Workstations
- Network Devices
- Logs
Tools:
Microsoft Sentinel
Custom Sources
- Databases
- Applications
Tools:
Microsoft Sentinel
IoT/OT
- Manufacturing
- Health Care
- Utilities
- Energy
Tools:
Internet of Things
Microsoft Defender for IoT
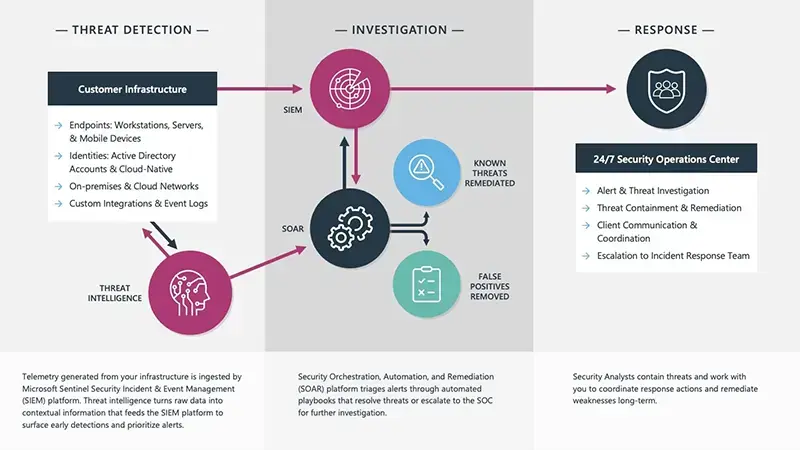
How MDR Works
Watch video below or view this graphic
Why Choose ProArch for Managed Detection and Response Service
24/7 Threat Resolution
The SOC remediates critical alerts; automation handles false positives and known alerts.
Fast Lane to Peace of Mind
100% remote cloud-based automated deployment and updates.
Use What You Already Have
Integrate your security stack into the SOC for instant monitoring and better ROI.
Strategic Advisory Sessions
Your dedicated advisor will work along side you to manage risk effectively.
ProArch-created Detection Rules
99% reduction in alert noise with new and managed threat detection rules.
Cost Effective. Goal Oriented.
Customized for budget and designed to align with long-term security goals.
ProArch is a MISA Member
Being in the Microsoft Intelligent Security Association means Microsoft validates our approach to defend against cyber threats.


Microsoft Partner You Can Trust
We are a top Microsoft Partner with Security designation & specializations, meeting consistent customer success, deep technical skills, and passing Microsoft audits.
What Our Customers Are Saying
We’ve made a lot of big strides on the security side in the last year, and Proarch has been a big part of that.
CIO, Healthcare
ProArch is helping us implement security best practices to stay compliant & ensure our cybersecurity is very locked down.
Plant Manager, Power and Energy
We quickly saw the level of support, ability, & tech resources ProArch had & realized they would be a much better partner.
CFO, Manufacturer
MDR FAQs
Why do companies need Managed Detection and Response?
Internal IT and security teams are struggling with the volume of threats and alerts. Companies need MDR (Managed Detection and Response) because it provides 24/7 threat monitoring and response, helping organizations detect and stop cyber threats that could otherwise go unnoticed. MDR fills internal talent gaps, offers strategic security guidance, and ensures regulatory compliance while remaining cost-effective.
What is the difference between an MDR service provider and a managed security service provider?
An MDR (Managed Detection and Response) service provider focuses on actively detecting and responding to threats in real-time. They use advanced tools and techniques to monitor your systems 24/7, quickly identify security incidents, and take immediate action to contain and mitigate threats.
A MSSP (Managed Security Service Provider) offers a broader range of security managed services, such as firewall management, vulnerability management, and general security monitoring, but may not provide the same level of active threat detection and response as MDR.
ProArch provides both MDR Services and Security Managed Services. Many of our clients leverage both programs for comprehensive protection across the organization.
How can MDR reduce the risk of ransomware?
MDR's continuous monitoring, use of threat intelligence, and SOC oversight reduce the window of opportunity for ransomware attacks to be successful. With 24/7 coverage, ransomware can be detected early, limiting the time it has to encrypt files and cause harm. This proactive and automated approach allows businesses to stay ahead of emerging ransomware threats and respond swiftly to minimize the impact on operations and data.
What remediation actions will the SOC take on behalf of the client?
As part of ProArch's Managed Detection and Response services the SOC remediates and responds to threat activity within its capabilities and integrated systems. Quarantining a system, restricting application execution, creating an investigation package, and performing advanced threat hunting to determine root cause are all handled by the SOC. In the case that a patch or other engineering function is required then the SOC communicates responsibility to the client. If successful compromise does occur, then transition to ProArch's Incident Response Team takes place.
Do MDR services help with compliance requirements?
MDR offers a significant improvement in meeting compliance requirements right from the start. Having an efficient MDR program in place, positions your organization to meet evolving state, federal, and industry standards. ProArch’s MDR services can be tailored to specific control requirements in standards like NIST, ISO, CMMC, NERC CIP, HIPAA, PCI, and others by maintaining a robust security posture and detailed audit and logging trails
Does MDR replace the need for other security services?
With security there is never a 100% guarantee. The goal of MDR is to improve your cyber resilience but it is not ‘all encompassing’ when it comes to all the elements of a mature security program. Security leaders must account for activities like vulnerability management, awareness training, pen testing, incident response planning, compliance, and security of specialized environments. ProArch's Security Team can assist with all of these components.
Do I still need an incident response plan if I have MDR?
MDR is not a replacement for a cybersecurity incident response plan. Although ProArch can perform incident response, those recovery and rebuild services are not included in the cost of MDR. It is important to have documented recovery playbooks that outline actions to be taken by members of your team, like contacting legal representation and restoring backups.
How long does it take to implement MDR services?
Most of the tools within ProArch’s MDR services can be deployed via code within 24 hours if the client provides administrative access to their Microsoft platforms. The rest of the configuration and fine-tuning can take anywhere from 30 to 60 days depending on the complexity of your environment. Our team works closely with you to ensure a smooth and efficient implementation process.
How to choose an MDR service?
When choosing an MDR service and provider, there are several factors to consider. On top of evaluating the program for all the essentials−24/7 monitoring, detection across the attack surface, automated remediation capabilities, skilled security operations center−it’s also important to find an MDR provider that has experience in your industry and can align the program to your organizations goals. If you’re looking for an MDR provider that will work alongside you to improve your security posture long-term, contact ProArch.
Why choose ProArch for Managed Detection and Response (MDR)?
ProArch MDR combines 24/7 SOC monitoring with automation to reduce alert noise, accelerate response times, and integrate seamlessly with existing Microsoft and third-party security tools. Our MDR services are designed for mid to large US enterprises that require continuous threat detection and response without the complexity of managing an in-house SOC.